How To Extract Sensible Information From Dump Du Schéma Ad

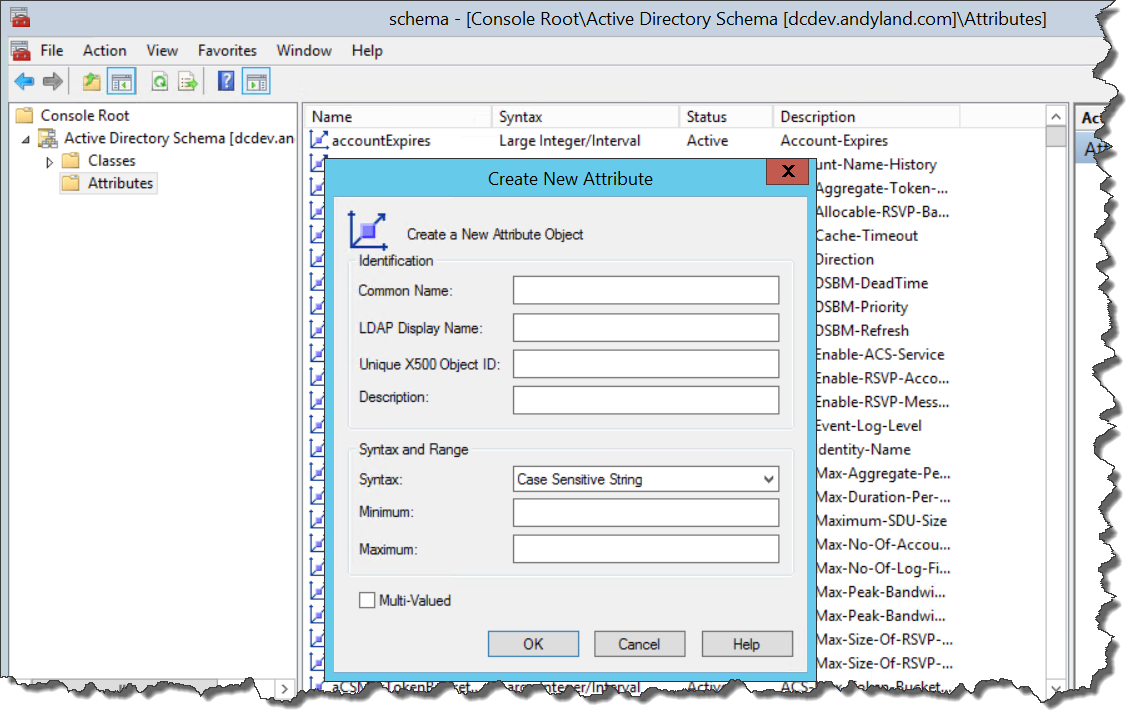
The Microsoft Active Directory schema contains formal definitions of every object class that can be created in an Active Directory forest. The schema also contains formal definitions of every attribute that can exist in an Active Directory object. This.
If you are able to logon to the target domain controller, alternative approach is to manually extract a snapshot of Active Directory database NTDS.dit using Volume Shadow Copy. I believe you can...
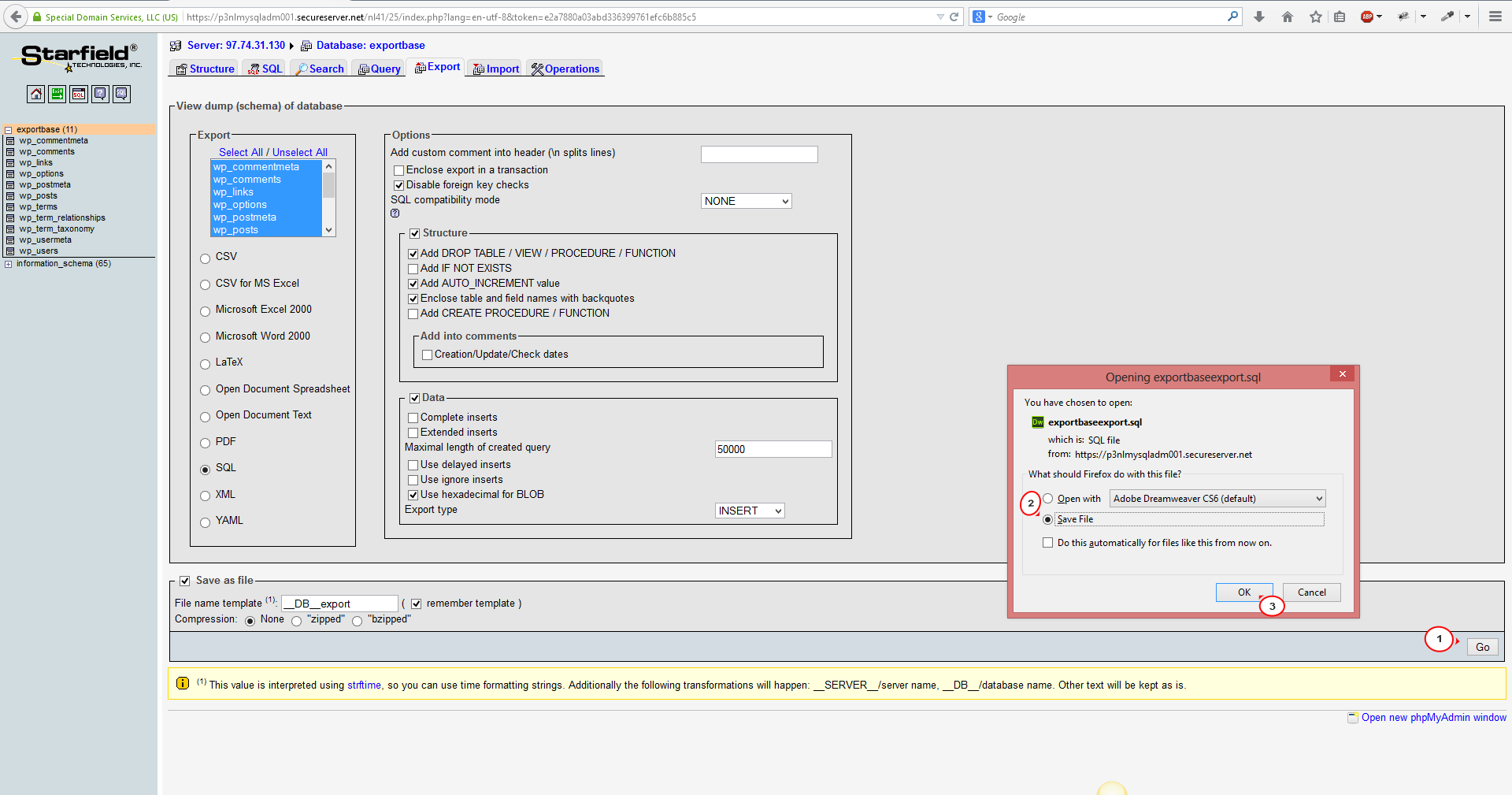
The following command will dump the table structure for all tables in the specified MySQL database: mysqldump -d -u someuser -p mydatabase The -d flag says not to include data in the dump. Alternatively you can use –no-data instead if you find that easier to remember:.
SAM and LSA secrets can be dumped either locally or remotely from the mounted registry hives. These secrets can also be extracted offline from the exported hives. Once the secrets are extracted, they can be used for various attacks, depending on the credential format..
Log into the Sensible app. Configure the extraction In the Document Types tab, Click New document type to create a new document type and name it "auto_insurance_quote." Leave the defaults and click Create. To upload an example document for your document type,.
11 Currently we are working on a monthly internal security test which among other should contain a verification of the real password strength the users choose. For this reason I want to extract the password hashes of all users via LDAP.
automate a dump of information_schema. I'm looking for a way to backup all the database on MySQL. I've written a batch file which runs mysqldump and it's working fine. Unfortunately I'm using MySQL 5.0 and can't upgrade to the newer version which.
Le schéma Microsoft Active Directory contient des définitions formelles de chaque classe d’objets qui peuvent être créées dans une forêt Active Directory. Le schéma contient également des définitions formelles de chaque attribut qui peut exister.
2 Answers Sorted by: 0 Ok Guys I fouund the Answer you need to first Create a Directory where the the dmp File is going to be. Then Import Like this: expdp USERNAME@server ip/SERVICE_NAME DIRECTORY=DIR_NAME.
Before you begin Before you create a Google Ads transfer, do the following: Verify that you have completed all actions required to enable the BigQuery Data Transfer Service. Create a BigQuery Data...
On systems using Windows Server 2008 and onwards, the easiest and most reliable way of dumping both Ntds.dit and the SYSTEM hive is to use Microsoft’s built-in tool ntdsutil. This automatically locates the files, takes a volume shadow copy, and.
Introduction DataDump Running DataDump Download Introduction When debugging or testing a digital forensic tool, or performing a data recovery procedure, you may have a requirement to extract some binary data from a forensic image or.
In order to extract the credentials you need the BOOTKEY, and that key is stored in the hive SYSTEM. The hashes can be extracted like this with impackets module secretsdump.py. python secretsdump.py LOCAL -sam sam.save -system system.save Domain Cached.
There are several tools out there that do this, including NTDS extract and Metasploit's Meterpreter. We can then parse that out and find the usernames and password hashes, and send them back. Now, the drawback of this is that it requires several things.
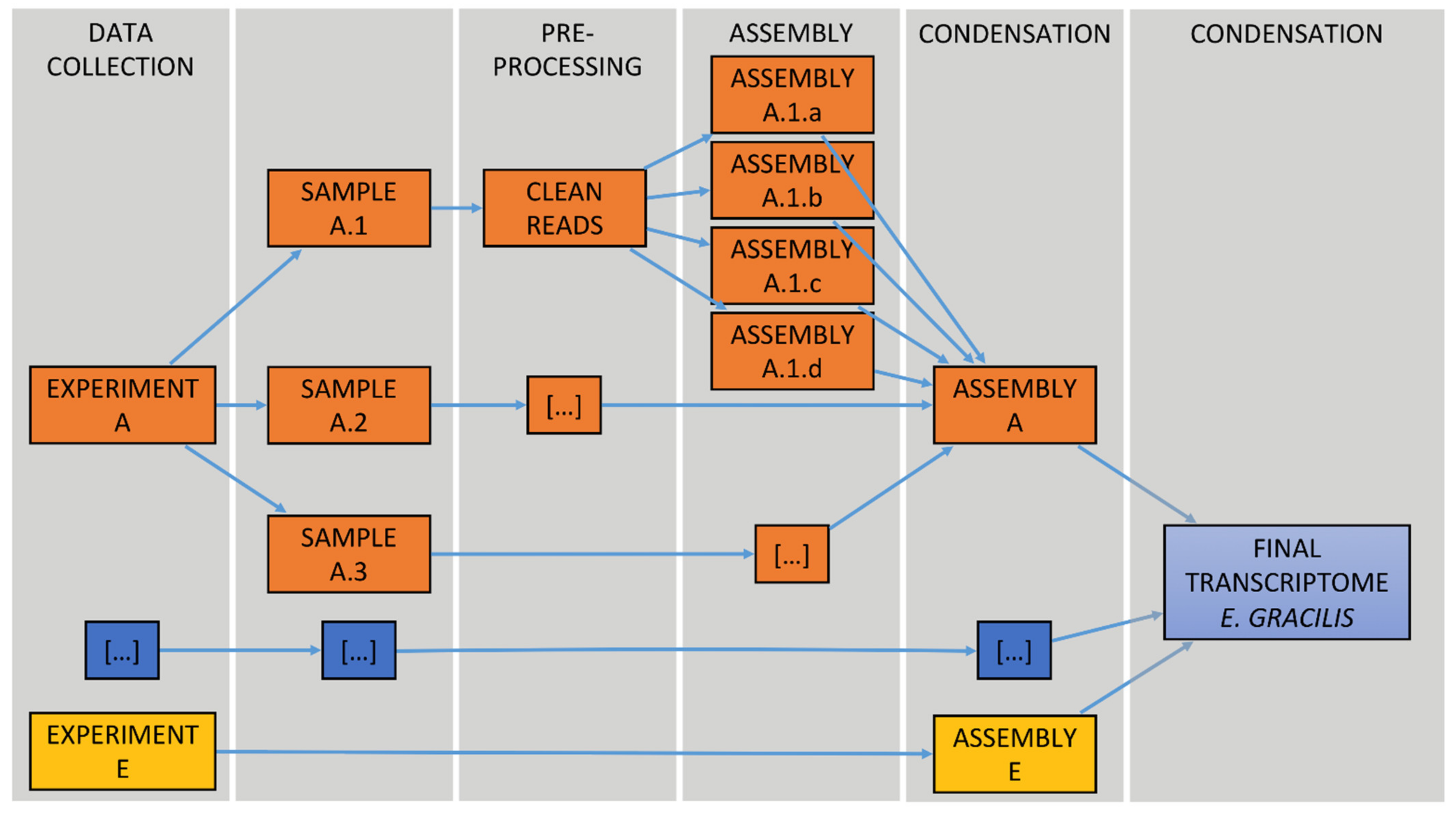
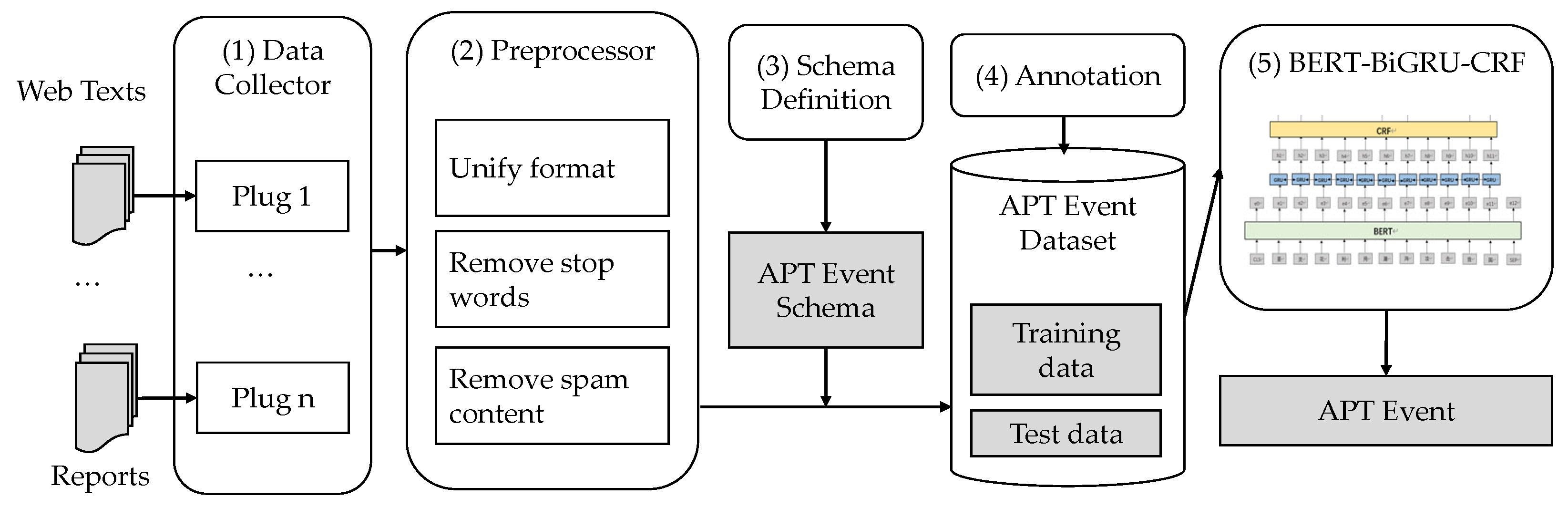
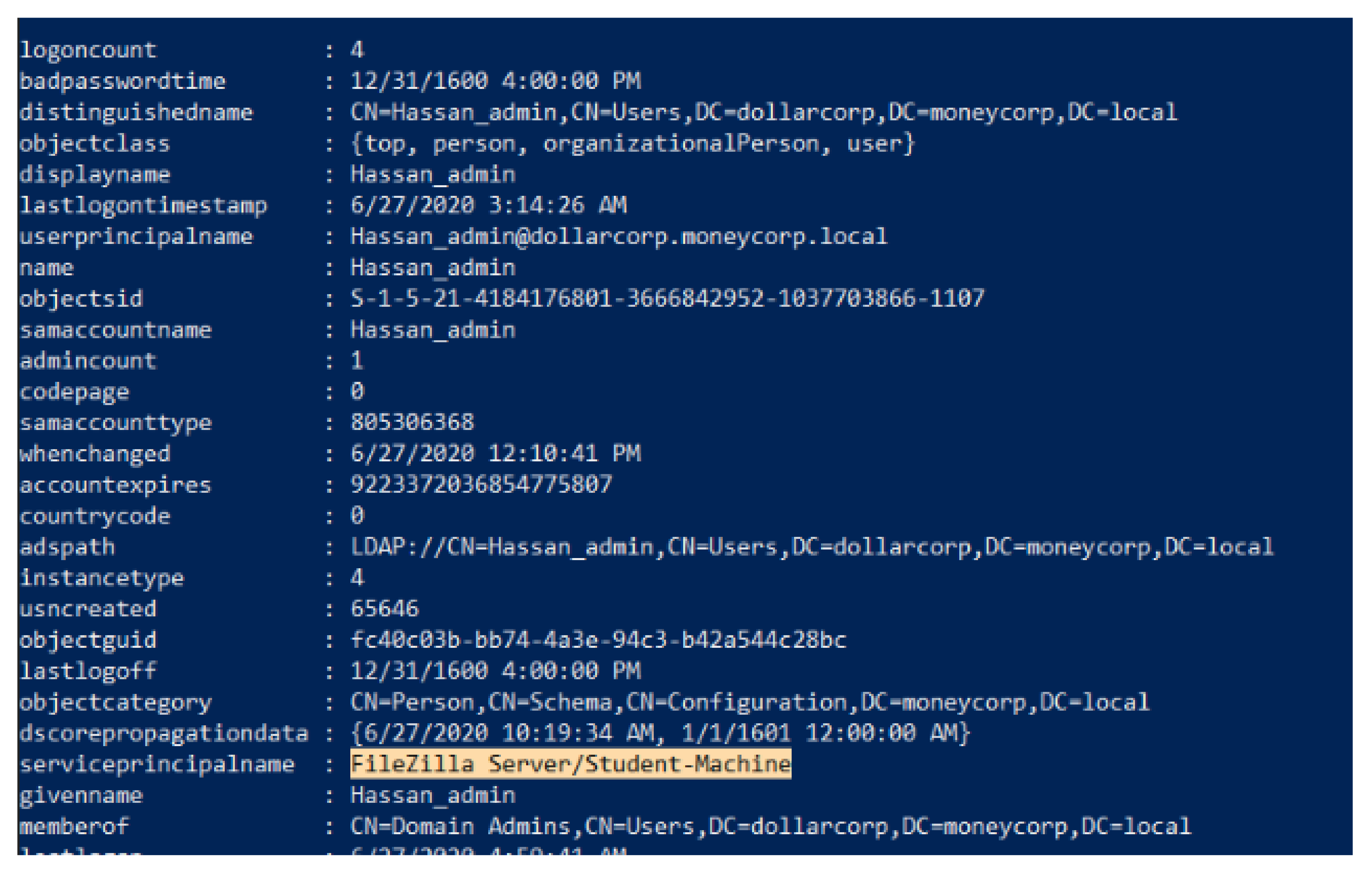
Active Directory Dump. During many penetration tests (or red versus blue team exercises), I have found myself with the need to investigate users, groups, computers and policies of a Windows domain. To do that, I have developed a series of PowerShell.
This article explains how to extract information from a dump file. Find the computer name in a kernel-mode dump file. Use the !peb extension if you need to determine the name of the computer on which the crash dump was made. Look for the value of.
Dans cet article. Lorsque les classes et/ou attributs existants ne correspondent pas au type de données que vous souhaitez stocker, vous pouvez étendre le schéma. Pour plus d’informations sur le choix du moment d’étendre le schéma,.
1. Microsoft-Signed Tools Out of all the options available, using Microsoft-signed binaries is an extremely convenient way to stealthily get a memory dump of LSASS, especially when they are already present on the workstation. Using these methods can.
The SRA toolkit is a collection of utilities that can dump, extract, and convert SRA data to different data formats. The vdb-decrypt utility included in the SRA toolkit can be used to decrypt any encrypted dbGaP data. The dbGaP data other than SRA (non-SRA.
Sometimes, it might be a dedicated tool just to extract a certain type of information from the dump and that’s it. Memory analysis can be endless, as we know, and it can be super short. One thing, which is sure, is that whatever works is always in the memory. In the memory.
How to protect sensitive data for its entire lifecycle in AWS | AWS Security Blog






Vous pourriez aussi aimer
- Exercices D anglais Sur Les Aliments Pdf
- Page De Garde Cahier Poésie Et Chant 2019 2020
- Les Différentes époques De L'histoire
- Legend Of Zelda Ocarina Of Time Manga
- Dandadan Chapter 119
- The Story Between A Dumb Prefect
- Page De Garde D Un Cahier De Mathématiques Collège
- Fate Makes No Mistakes Manhwa
- Page De Garde Cahier De Leçons Français Cm
- Page De Garde Cahier De Liaison Maternelle Pdf
- The Final Boss The Engineering Leader
- Onna Tomodachi To Kekkon Shitemita
- Page De Garde Cahier De Poésie Modifiable
- My Love Story With Yamada kun To Lv999 Manga
- Magic In Another World Is Too Far Behind
- What's The Weather Like Today Traduction
- When Is Rent A Girlfriend Season 3
- Coloriages Reine Des Neige A Imprimer
- Read Uncle From Another World
- Uzaki chan Wants To Hang Out Uncensored
